vnctf 2022 re复现
BabyMaze
.pyc的文件,第一反应是用uncompyle6来直接逆。当然啦,肯定不会是我想的这么简单,我还是太年轻了,这道题有花指令让uncompyle6没法用。所以得先去花指令然后才能用工具逆字节码。
去花指令
开始我们并不知道有花指令,所以我们先看看字节码,这里用python的marshal库和dis库来读取二进制pyc文件并反汇编成字节码来分析:
import dis,marshal
fp = open('BabyMaze','rb').read() #这里用open只是打开了一个文件,还得用read()把它读出来
code = marshal.loads(fp[16:]) #这里由于是3.0的python所以是要去除前16个文件头的,2.0是8个
print(dis.dsi(code))
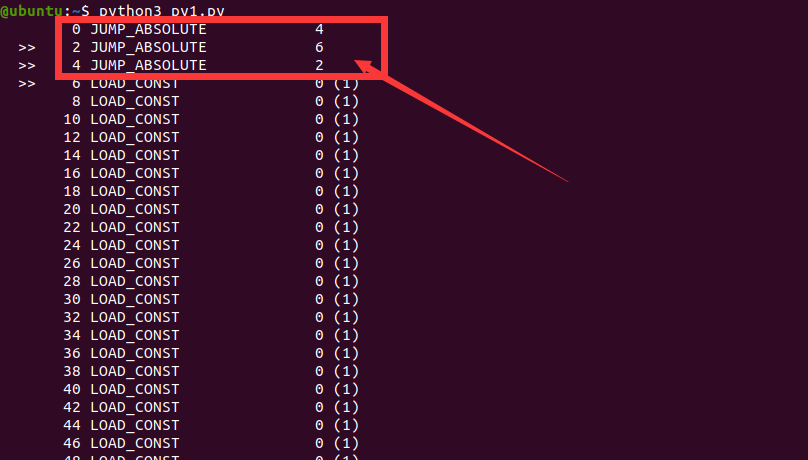
结果如上图,在pyc中存在着花指令,我们需要在pyc中定位这部分的机器码,然后去掉就行,下面我们来去掉它。
这是关于字节码对应机器码的数字(https://www.jianshu.com/p/f540e540f940),我们根据这个数字对应在二进制文件中修改。
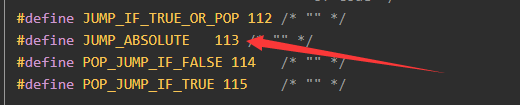
查找得出JUMP_ABSOLUTE的机器码为113即0x71,用010打开
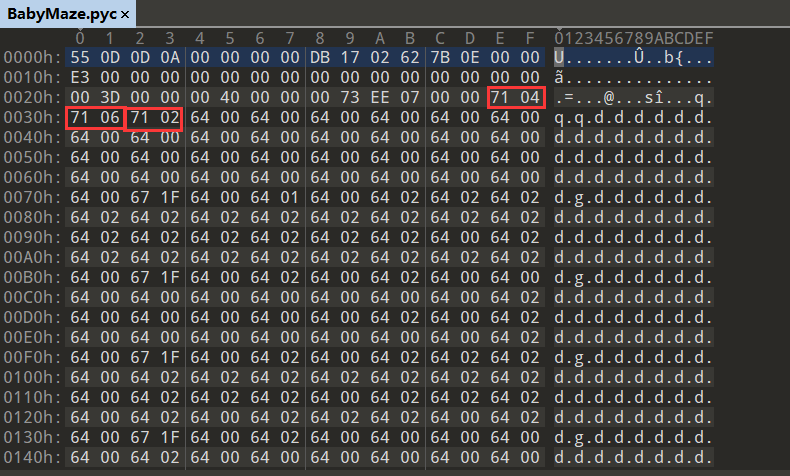
刚好三个,到这里我们就已经找到了机器码的位置了,下面我们只需要把它们去掉就行,但是在去掉后要注意改python文件头中记录代码长度的数据。这个数据可以通过下面的这行代码找到
print(hex(len(code.co_code)))
得出改前代码的长度为0x7ee,在上图的二进制文件中找到0x7ee这段数据,就在红色框前面不远处,把这它改为0x7E8(0x7ee-2)。改完后保存文件,就可以用uncompyle6了。
下面是最终得出的python代码。
_map = [
[
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1],
[1, 5, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1],
[1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 7, 1],
[1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1]]
def maze():
x = 1
y = 1
step = input()
for i in range(len(step)):
if step[i] == 'w':
x -= 1
else:
if step[i] == 's':
x += 1
else:
if step[i] == 'a':
y -= 1
else:
if step[i] == 'd':
y += 1
else:
return False
if _map[x][y] == 1:
return False
if x == 29 and y == 29:
return True
这是弄出来的python代码,显然这是一个迷宫题,采用深度优先搜索就出来了。代码放在下面:
#include <stdio.h>
#include <windows.h>
char map[31][31] = {
{1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1},
{1, 5, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1},
{1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1},
{1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1},
{1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1},
{1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1},
{1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1},
{1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1},
{1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1},
{1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1},
{1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1},
{1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1},
{1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1},
{1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1},
{1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1},
{1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1},
{1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1},
{1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1},
{1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1},
{1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1},
{1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1},
{1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1},
{1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1},
{1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 7, 1},
{1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1}
};
char flag[1000]="\\0";
void DFS (int x,int y,int n){
if(map[x][y]==1){
return;
}
if(map[x][y]==7){
flag[n]='\\0';
printf("%s",flag);
exit(0);
}
flag[n]='s';
map[x][y]=1;//将走过的路径标记一下防止走回去
DFS(x+1,y,n+1);
flag[n]='w';
map[x][y]=1;
DFS(x-1,y,n+1);
flag[n]='a';
map[x][y]=1;
DFS(x,y-1,n+1);
flag[n]='d';
map[x][y]=1;
DFS(x,y+1,n+1);
}
int main(){
DFS(1,1,0);
printf("%s",flag);
return 0;
}
//输出ssssddssaassddddwwwwddwwddddddwwddddddssddwwddddddddssssaawwaassaassaassddssaassaawwwwwwaaaaaaaassaassddddwwddssddssssaassddssssaaaaaawwddwwaawwwwaassssssssssssddddssddssddddddddwwaaaaaawwwwddssddwwwwwwwwddssddssssssssddddss
将输出md5一下,得出flag为:vnctf{801f190737434100e7d2790bd5b0732e}
时空飞行
首先
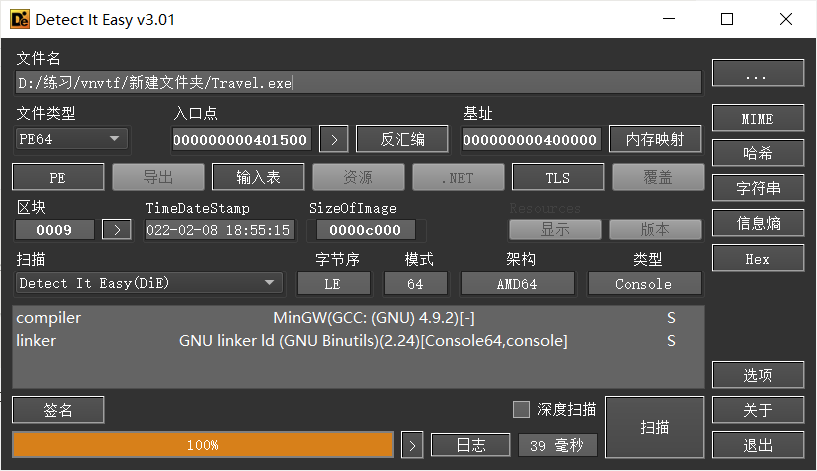
无壳且64位。丢入ida分析一手。
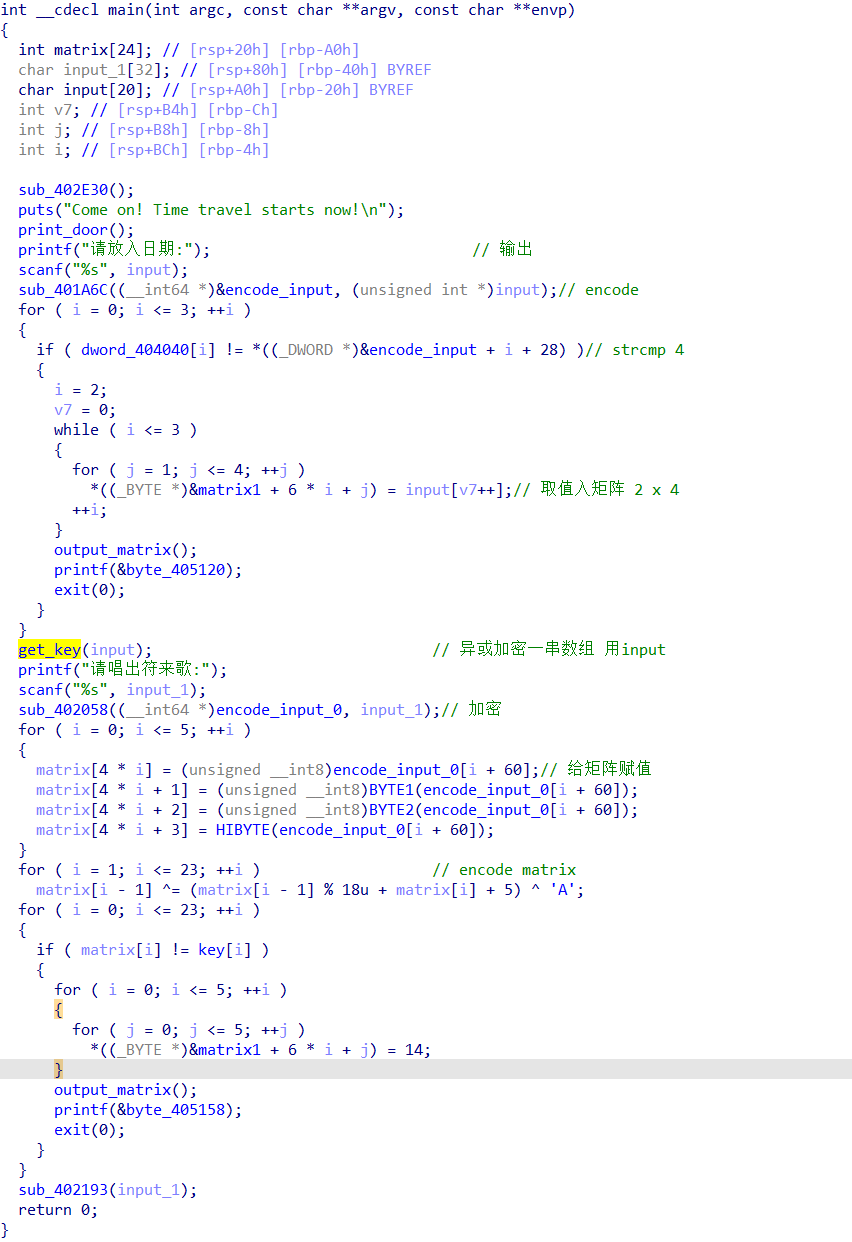
分析出大致逻辑,先输入一组数据进入一个函数加密,判断正确后,由输入的数据得到一个秘钥,带上这组秘钥又输入一组数据进入一个函数加密,再将加密后的数据再进行了多次不可逆的异或加密,最后比较是否成功。
分析函数
进入第一个函数分析了一下,没看出这是一个不带S盒的DES加密,
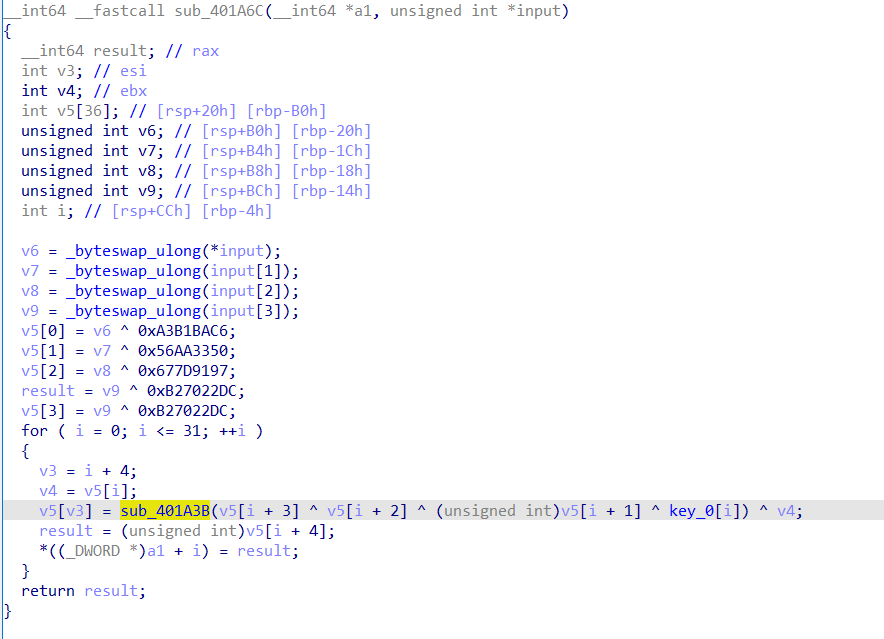
后来知道这是一个DES之后就有会了,由于DES加密算法是对合算法,也就是说DES解密和加密可以共用同一运算(只是子密钥使用的顺序不同),所以我们直接写解题脚本:
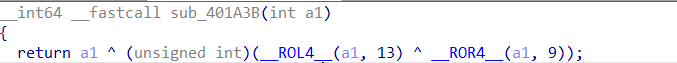
但是要注意的是ida的这个函数是指循环移动一个数,比如一个数是12345循环向右移动2位就是45123
#include <stdio.h>
#include <windows.h>
unsigned ROL4(unsigned int value, unsigned int count)
{
const unsigned int nbits = sizeof(unsigned int) * 8;
count %= nbits;
unsigned int low = value >> (nbits - count);
value <<= count;
value |= low;
return value;
}
unsigned int fun(unsigned int a1){
return a1 ^ (ROL4(a1, 13) ^ ROL4(a1, 23));
}
int main(){
unsigned int key[32] = {
0x00070E15, 0x1C232A31, 0x383F464D, 0x545B6269, 0x70777E85, 0x8C939AA1, 0xA8AFB6BD, 0xC4CBD2D9,
0xE0E7EEF5, 0xFC030A11, 0x181F262D, 0x343B4249, 0x50575E65, 0x6C737A81, 0x888F969D, 0xA4ABB2B9,
0xC0C7CED5, 0xDCE3EAF1, 0xF8FF060D, 0x141B2229, 0x30373E45, 0x4C535A61, 0x686F767D, 0x848B9299,
0xA0A7AEB5, 0xBCC3CAD1, 0xD8DFE6ED, 0xF4FB0209, 0x10171E25, 0x2C333A41, 0x484F565D, 0x646B7279
};
unsigned int result[4] = {
0xFD07C452, 0xEC90A488, 0x68D33CD1, 0x96F64587
};
static const unsigned long FK[4] = {0xa3b1bac6,0x56aa3350,0x677d9197,0xb27022dc};
unsigned int input[36]={ 0, };
input[35] = result[3];
input[34] = result[2];
input[33] = result[1];
input[32] = result[0];
for ( int i = 35; i >= 4; i-- )
input[i - 4] = input[i] ^ ( fun(input[i - 3] ^ input[i - 2] ^ input[i - 1] ^ key[i - 4]) );
int t[4];
for(int i=0;i<4;i++){
t[i] = input[i]^FK[i];
}
unsigned char * p = (unsigned char *)t;
for ( int i = 1; i <= 2; i++ ){
for ( int j = 1; j <= 4; j++ )
printf("%c", p[i * 4 - j]);
}
return 0;
}
#输出20211205
当我们第一个输入确定之后,那么
这个就是一个固定值我们直接动态调试就可以出来。
第二个加密函数
同样的我也没能看出来是简化的AES加密,继续分析,这里比较复杂,得到AES加密后的数据,需要先出下面的异或加密,这个异或加密了次,破坏了加密的结构,所以没办法直接计算出来,所以我们得爆破它
爆破的函数如下,这里还是用了递归的方式来爆破的
unsigned char flag[24]={0,};
unsigned char flags[40][24]={0,};// 由于我们不能确定爆破出来的哪一个是真正的答案,所以需要储存多个答案去尝试
unsigned int result[24] = {
0x00000025, 0x00000015, 0x000000DF, 0x000000A2, 0x000000C0, 0x00000093, 0x000000AD, 0x00000014,
0x00000046, 0x000000C5, 0x0000000F, 0x0000002E, 0x0000009A, 0x000000EB, 0x00000030, 0x000000F8,
0x00000020, 0x000000E9, 0x000000CB, 0x00000088, 0x000000C6, 0x000000BE, 0x0000008D, 0x000000E3
};
int x=0;
void fun(unsigned char flag[], int n){
int i=0;
if(n==0){
for(i=0;i<24;i++){
flags[x][i]=flag[i];
}
x++;
}
else{
for(i=0;i<=0xff;i++){
flag[23]=0xe3;
if(((i%18+flag[n]+5)^('A'^i))==result[n-1]){
flag[n-1]=i;
fun(flag,n-1);
}
}
}
}
接着就可以开始逆向这个AES加密了,这里我直接结合上面写出完整的代码:
#include <stdio.h>
unsigned char flag[24]={0,};
unsigned char flag1[40][24]={0,};
int x=0;
unsigned int result[24] = {
0x00000025, 0x00000015, 0x000000DF, 0x000000A2, 0x000000C0, 0x00000093, 0x000000AD, 0x00000014,
0x00000046, 0x000000C5, 0x0000000F, 0x0000002E, 0x0000009A, 0x000000EB, 0x00000030, 0x000000F8,
0x00000020, 0x000000E9, 0x000000CB, 0x00000088, 0x000000C6, 0x000000BE, 0x0000008D, 0x000000E3
};
unsigned int key[10] = {
0x01000000, 0x02000000, 0x04000000, 0x08000000, 0x10000000, 0x20000000, 0x40000000, 0x80000000,
0x1B000000, 0x36000000
};
void fun(unsigned char flag[], int n){
int i=0;
if(n==0){
for(i=0;i<24;i++){
flag1[x][i]=flag[i];
}
x++;
}
else{
for(i=0;i<=0xff;i++){
flag[23]=0xe3;
if(((i%18+flag[n]+5)^('A'^i))==result[n-1]){
flag[n-1]=i;
fun(flag,n-1);
}
}
}
}
unsigned int T(unsigned int t,int num){
int tmp[4]={0};
tmp[0]=(t>>24)&0x000000ff;
tmp[1]=(t>>16)&0x000000ff;
tmp[2]=(t>>8)&0x000000ff;
tmp[3]=t&0x000000ff;
int tmp_tmp[4]={0};
for(int i=0;i<4;i++){
tmp_tmp[i]=tmp[i];
}
for(int i=0;i<4;i++){
tmp[i]=tmp_tmp[(i+1)%4];
}
int a=(tmp[3]|(tmp[2]<<8)|(tmp[1]<<16)|(tmp[0]<<24));
return (a^key[num]);
}
int main(){
unsigned int encode_input[32] = {
0x690D09C1, 0xE87CF612, 0x1E2ED4FF, 0x52B950DD, 0x66EDF1E1, 0xC22A395A, 0x088BF969, 0x43EB9D37,
0x418AB9FC, 0xD7CEE4DF, 0xC51AFE95, 0x670222D4, 0x35467B04, 0x75263090, 0x3BDB424A, 0x1C91EA0C,
0xCCE40AF9, 0xCC791893, 0x9517B940, 0x2DE0DBF9, 0x9772FAA3, 0x4A515DF3, 0xE6AD7684, 0x9C53ADF5,
0x19B42481, 0x239397B9, 0xF73DD48D, 0x5719BFC7, 0xFD07C452, 0xEC90A488, 0x68D33CD1, 0x96F64587
};
flag[23]=0xe3;
fun(flag,23);
unsigned int * pi=(unsigned int *)flag1;
unsigned int t[66]={0};
for(int i=0;i<40;i++){
for(int j=60;j<66;j++){
t[j]=pi[i*6+j-60];
}
int num=9;
for(int k=65;k>=6;k--){
if(k%6){
t[k-6]=t[k]^t[k-1];
}
else{
t[k-6]=t[k]^T(t[k-1],num);
num--;
}
}
unsigned char * p = (unsigned char *)t;
for ( int i = 0; i < 24; i += 4 ){
printf("%c%c%c%c", p[i + 3], p[i + 2], p[i + 1], p[i]);//注意⼩端序
}
printf("\n");
}
return 0;
}
输出结果
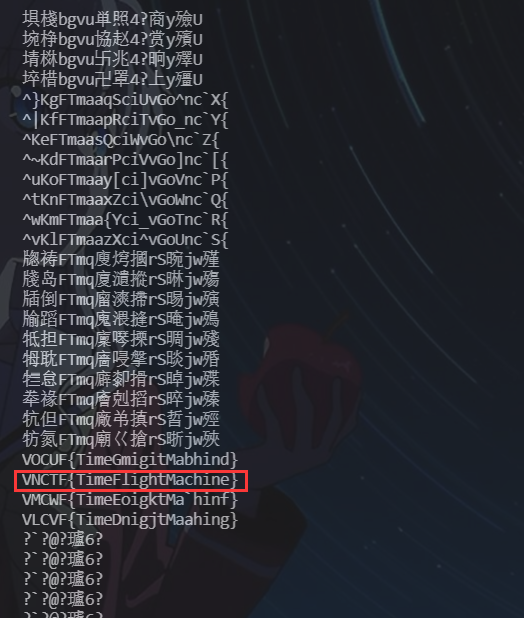
VNCTF{TimeFlightMachine}这还不是最后的结果,我们得把得到的这些数据输回题目中
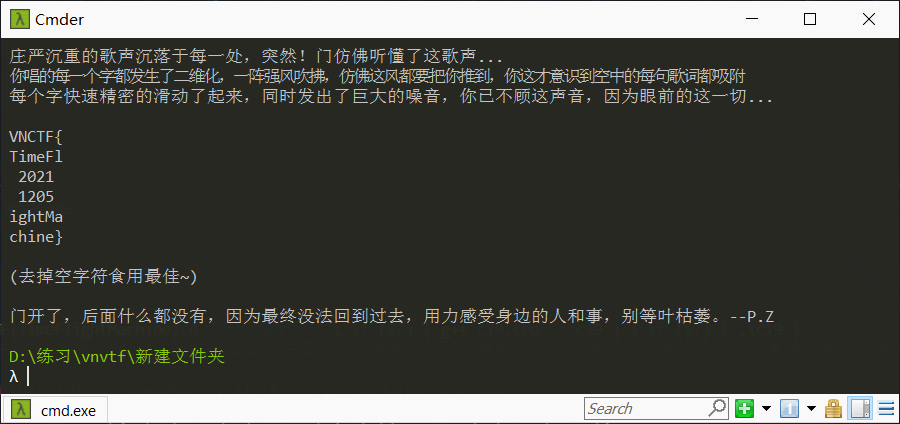
最后得出flag:VNCTF{TimeFl20211205ightMachine}
CM狗
这道题运用了go语言的vm技术模拟了一个tea加密
首先
无壳且64位。丢入ida分析
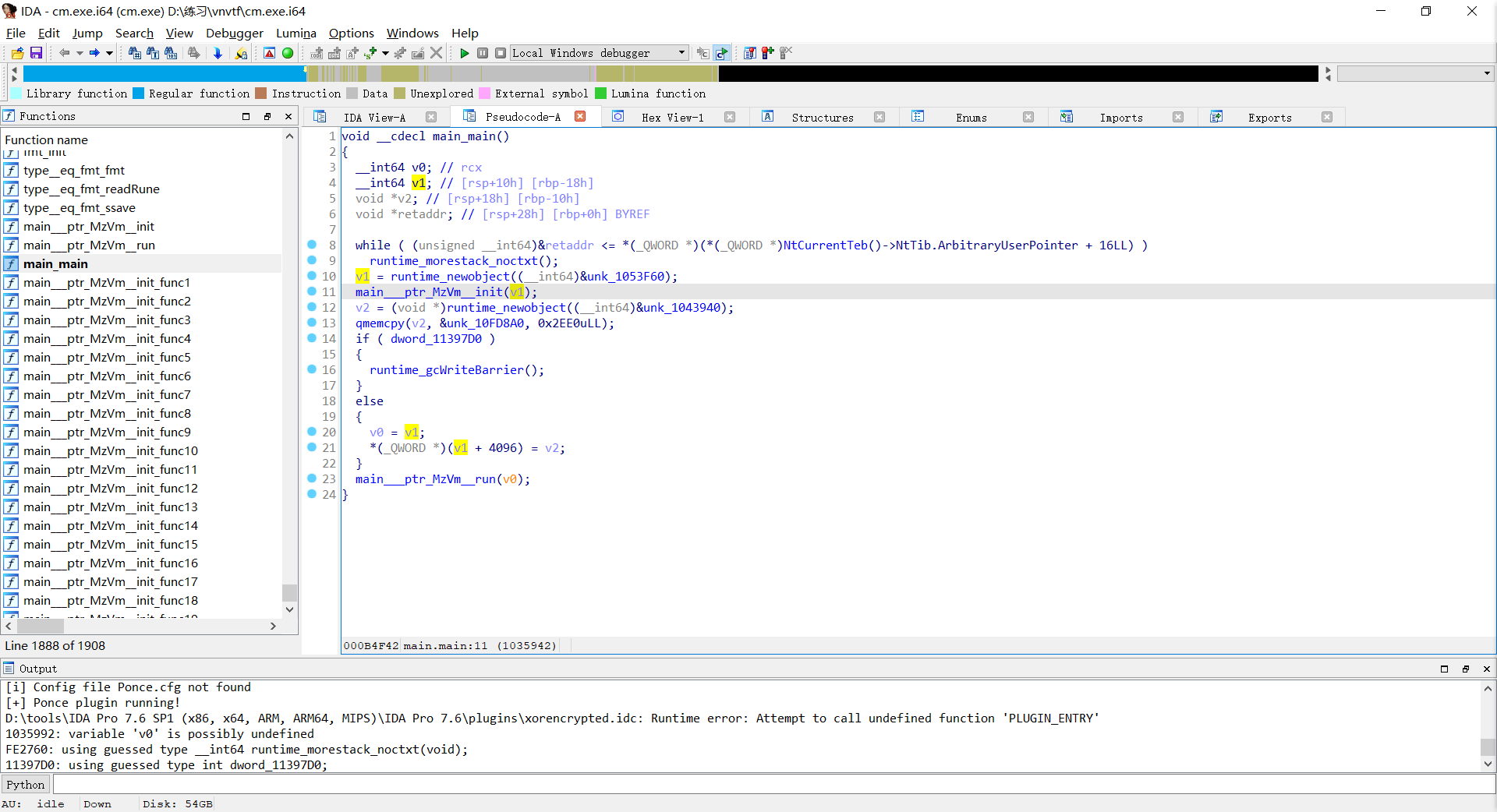
还好go没去符号直接找到main函数进去看看
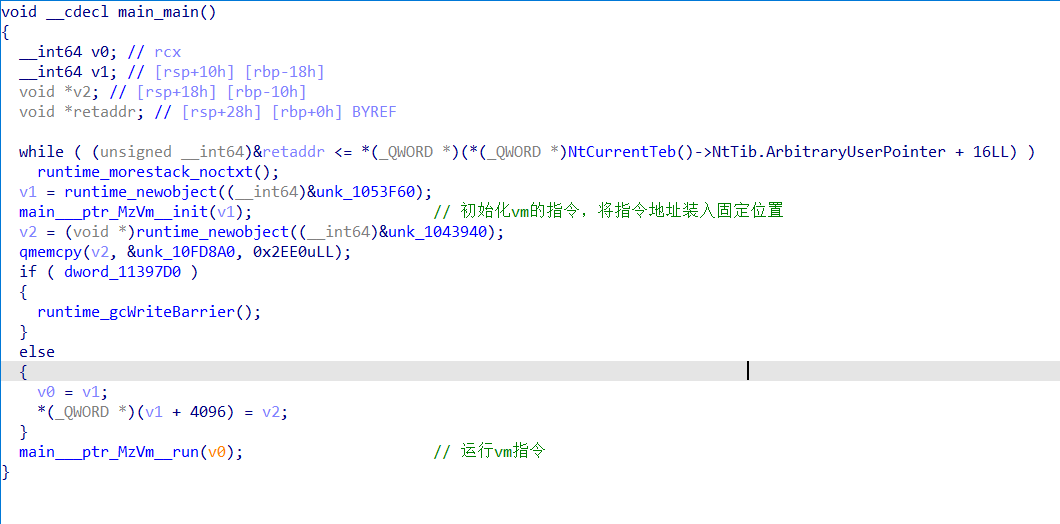
只有两个有用的函数,我们直接看run函数,我弄vm是通过直接看汇编,然后在每个指令的前面下断来分析哪个函数是哪个指令,找到寄存器位置,以及分清操作数与操作符。
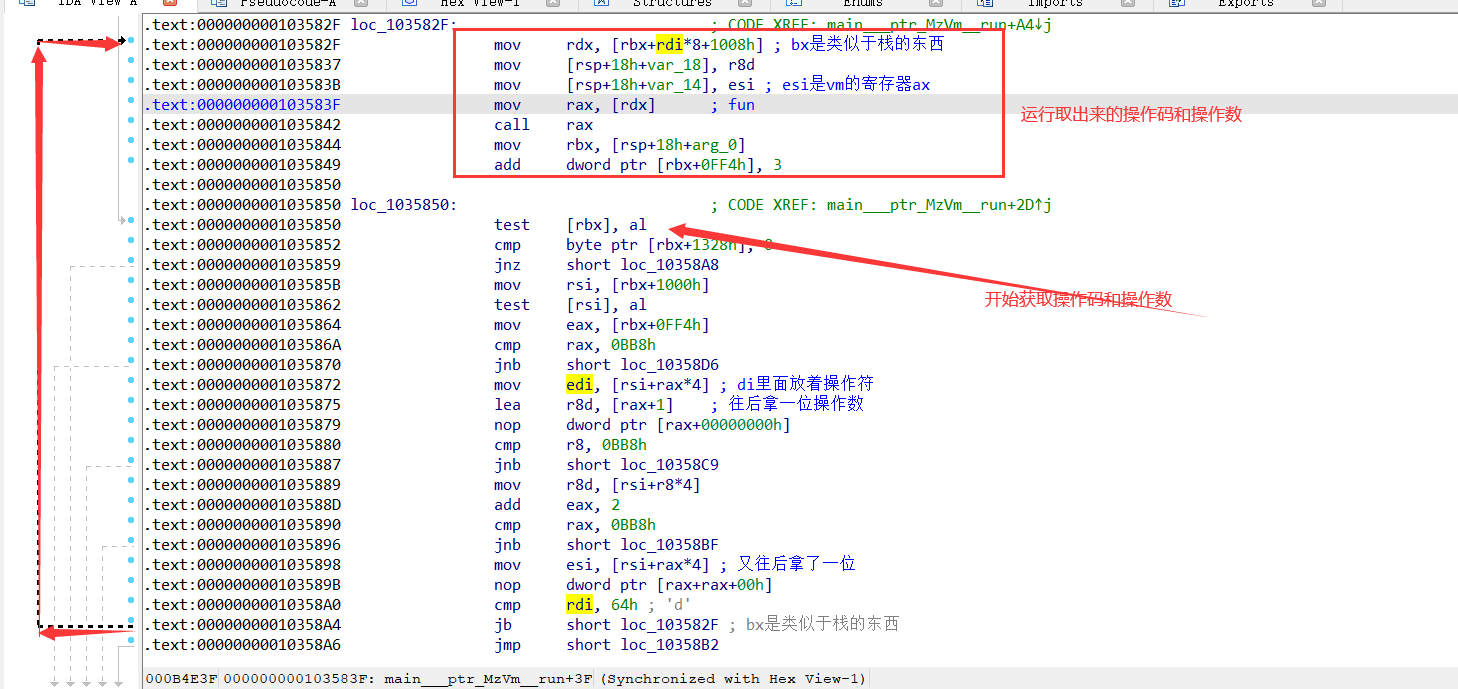
这是刚进入run函数的时候,经过分析发现大致过程就是先取一个操作符,然后拿两个操作数出来,跳转到上面去运行。
依次在每一个函数前面下断点
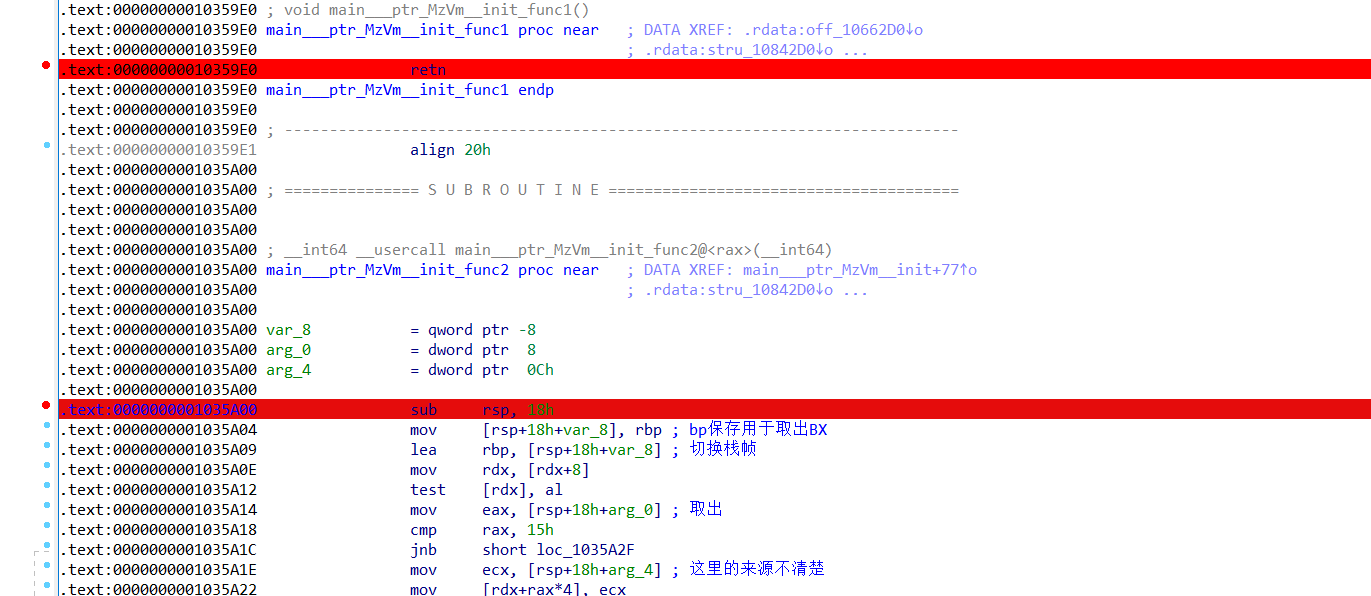
动态调试起来判断每一个函数代表的汇编指令,但是有几个函数在程序结束的时候都没有用到,这是中间有提前退出了,我们只能通过静态分析,去弄,虽然有点麻烦但是还是可以解决。分析出每个函数代表的汇编指令入下
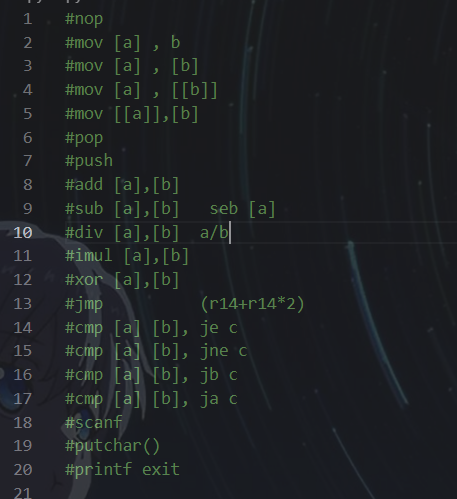
我这个分析的太粗糙了,没有发现数字之间的内在的联系,这里的a,b,c与题中给的操作数是有关系的,我这样分析出来导致了我没办法进行下一步的操作。这里我抄Mas0n大佬的wp。
from string import printable
_m = list(printable.encode())
_m.remove(10)
_m.remove(13)
_hex = lambda _d: "0x"+hex(_d)[2:].zfill(2) if _d > 15 else _d
_chr = lambda _v: hex(_v) if _v not in _m else "'{ch}'".format(ch=chr(_v))
maps = {
0x1: "nop",
0x2: "mov R[{num}], {right} ; {ch}",
0x3: "mov R[{num}], R[{right}]",
0x4: "mov R[{num}], Memory[{right}]",
0x5: "mov Memory[num] R[{right}]",
0x6: "push R[{num}]",
0x7: "pop R[{num}]",
0x8: "add R[{num}], R[{right}]",
0x9: "dec R[{num}], R[{right}]",
0xa: "div R[{num}], R[{right}]",
0xb: "mul R[{num}], R[{right}]",
0xc: "xor R[{num}], R[{right}]",
0xd: "jmp R[{num}]",
0xe: "cmp R[{num}] R[{right}], je R[19]",
0xf: "cmp R[{num}] R[{right}], jne R[19]",
0x10: "cmp R[{num}] R[{right}], jb R[19]",
0x11: "cmp R[{num}] R[{right}], ja R[19]",
0x62: "getchar R[{num}]",
0x63: "putchar R[{num}]",
0x64: "vm quit"
}
data = [0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000057, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006C, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000063, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006D, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000074, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000056, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000004E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000043, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000054, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000046, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000030, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000021, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000000A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000069, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000070, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000075, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000074, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000066, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006C, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000061, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000067, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000003A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000000A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000013, 0x00000049, 0x00000001, 0x00000003, 0x00000000, 0x00000001, 0x00000001, 0x0000002B, 0x00000001, 0x00000002, 0x00000001, 0x00000061, 0x00000000, 0x00000000, 0x00000005, 0x00000000, 0x00000000, 0x00000008, 0x00000001, 0x00000002, 0x0000000E, 0x00000001, 0x00000003, 0x00000001, 0x00000000, 0x00000000, 0x00000005, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000002, 0x00000000, 0x00000006, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000002, 0x00000000, 0x00000006, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000002, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000002, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000009, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000009, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000002, 0x00000000, 0x0000000A, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000002, 0x00000000, 0x0000000A, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000002, 0x00000000, 0x0000000B, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000002, 0x00000000, 0x0000000B, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000002, 0x00000000, 0x0000000C, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000002, 0x00000000, 0x0000000C, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000002, 0x00000000, 0x0000000D, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000002, 0x00000000, 0x0000000D, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000E, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000E, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000E, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000E, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000F, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x0000000F, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000F, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x0000000F, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000F, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000F, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x00000010, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x00000010, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000010, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000005, 0x00000006, 0x00000000, 0x00000005, 0x00000007, 0x00000000, 0x00000005, 0x00000008, 0x00000000, 0x00000005, 0x00000009, 0x00000000, 0x00000005, 0x0000000A, 0x00000000, 0x00000005, 0x0000000B, 0x00000000, 0x00000005, 0x0000000C, 0x00000000, 0x00000005, 0x0000000D, 0x00000000, 0x00000005, 0x0000000E, 0x00000000, 0x00000005, 0x0000000F, 0x00000000, 0x00000005, 0x00000010, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x0000011C, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0xE8D1D5DF, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0xF5E3C114, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x00000127, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x228EC216, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x89D45A61, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x00000132, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x655B8F69, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x2484A07A, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x0000013D, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0xD9E5E7F8, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x3A441532, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x00000148, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x91AB7E88, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x69FC64BC, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x007D3765, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x00000189, 0x0000000C, 0x00000000, 0x00000000, 0x00000063, 0x00000000, 0x00000000, 0x00000001, 0x00000003, 0x9E3779B9, 0x00000001, 0x00000004, 0x00095C4C, 0x00000001, 0x00000005, 0x0000871D, 0x00000001, 0x00000006, 0x0001A7B7, 0x00000001, 0x00000007, 0x0012C7C7, 0x00000001, 0x00000008, 0x00000000, 0x00000001, 0x00000011, 0x00000010, 0x00000001, 0x00000012, 0x00000020, 0x00000001, 0x00000013, 0x00000160, 0x00000001, 0x0000000A, 0x00000000, 0x00000001, 0x0000000B, 0x00000020, 0x00000001, 0x0000000C, 0x00000001, 0x00000007, 0x00000008, 0x00000003, 0x00000002, 0x00000000, 0x00000002, 0x0000000A, 0x00000000, 0x00000011, 0x00000007, 0x00000000, 0x00000004, 0x00000002, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x00000002, 0x00000007, 0x00000000, 0x00000008, 0x00000002, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x00000002, 0x00000009, 0x00000000, 0x00000012, 0x00000007, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000B, 0x00000000, 0x0000000F, 0x0000000B, 0x00000000, 0x00000010, 0x00000007, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000001, 0x0000000A, 0x00000000, 0x00000011, 0x00000007, 0x00000000, 0x00000006, 0x00000002, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x00000001, 0x00000007, 0x00000000, 0x00000008, 0x00000002, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x00000001, 0x00000009, 0x00000000, 0x00000012, 0x00000007, 0x00000000, 0x00000007, 0x00000002, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000B, 0x00000000, 0x0000000F, 0x0000000B, 0x00000000, 0x00000010, 0x00000007, 0x00000002, 0x00000000, 0x00000008, 0x0000000B, 0x0000000C, 0x0000000E, 0x0000000B, 0x0000000A, 0x0000000C, 0x00000014, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x0000000C, 0x00000014, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000079, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000073, 0x00000062, 0x00000000, 0x00000000, 0x0000000C, 0x00000014, 0x00000000]
for i in range(0, len(data), 3):
funcItem, arg1, arg2 = data[i], data[i+1], data[i+2]
# print(funcItem+1, arg1, arg2)
print(hex(i // 3).rjust(5, " ")+":", maps[funcItem+1].format(num=arg1, right=_hex(arg2), ch=_chr(arg2)))
这种方法翻译汇编是学到了很多,接下来就是比较烦人的了,根据输出人肉反汇编代码,这里直接写,tea加密的逆向算法,与DES加密相似,加密与解密是同一函数,所以只需要逆回去就好。
void fun(uint* v,uint* k){
uint v0=v[0],v1=v[1],sum=0xC6EF3720,i;
uint delta=0x9e3779b9;
uint k0=k[0],k1=k[1],k2=k[2],k3=k[3];
for(i=0;i<32;i++){
v1-=((v0<<4)+k2)^(v0+sum)^((v0>>5)+k3);
v0-=((v1<<4)+k0)^(v1+sum)^((v1>>5)+k1);
sum-=delta;
}
v[0]=v0;
v[1]=v1;
}
得出flag为VNCTF{ecd63ae5-8945-4ac4-b5a5-34fc3ade81e7}
总结
复现完这套题获益良多,更加透彻的了解各种基础的加密原理,,比赛的时候并没有做出来,感觉在比赛的时候没办法静下心来一行一行的分析代码。我还是太菜啦,被简单的pyc的花指令就给打住了。
 发表于 2022-3-10 11:04
发表于 2022-3-10 11:04
 |
发表于 2022-3-10 14:20
|楼主
|
发表于 2022-3-10 14:20
|楼主 发表于 2022-3-13 13:03
发表于 2022-3-13 13:03